How to Configure Impersonation to Deploy the Solution [MS Exchange On-Premises]¶
For users of the Email Sidebar on:
9 min read
Tip
Refer to this article to learn how to set up Impersonation in case your company uses an Office 365 mail server or to this article for Hybrid mail servers
Note
All configuration activities described in this article are typical actions performed for an Impersonation service account via Exchange Admin portal secured by Microsoft. On RG Email Sidebar side, data processing privacy and security are guaranteed by the applicable Revenue Grid policies
Also see the following articles to learn more about MS Exchange Impersonation:
Enabling MS Exchange Impersonation in RG Email Sidebar consists of three Stages:
I. Create a Service Account and Apply it for RGES end users [described in this section]
II. Verify the Configuration [described in this section]
III. Configure Exchange Impersonation in RG Email Sidebar’s Admin panel [described in a dedicated KB article]
Stage I: Configure a Service Account and Apply it for RGES End Users¶
In order to set up an Exchange Impersonation account via Exchange Admin Center, follow the steps below.
Setup via Exchange Admin Center [main method]¶
In order to set up an Exchange Impersonation account via Exchange Admin Center, follow the steps below.
1. Create a Service Account¶
First, you need to create a Service email account. It must to be a dedicated mailbox used only as an Impersonating service account for RG Email Sidebar, it should have no other functions. The Impersonating service account requires a dedicated MS Exchange / Office 365 mailbox license E1, E3, E5, Business Basic or Business Standard and does not require an extra RG Email Sidebar license.
Please register the Service Account with the name MasterImpersonation to make it easy to find later for testing or troubleshooting.
Follow the steps described in this Microsoft article to create a Service mail account.
2. Create a Group that Includes All RGES End Users’ accounts¶
Depending on your Org’s configuration, you may use A) a Distribution group or B) a Security group list.
A. To create a Distribution group¶
2.A.1. Log in to your corporate Exchange Admin Center with Admin credentials and select the tab Exchange in the upper left corner
Exchange Admin portal link: https://admin.microsoft.com/Adminportal/Home
>>> Click to see a screenshot <<<
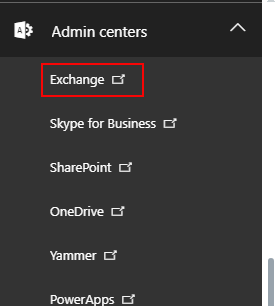
2.A.2. Select recipients in the navigation pane on the left and then click groups in the right-hand pane
>>> Click to see a screenshot <<<
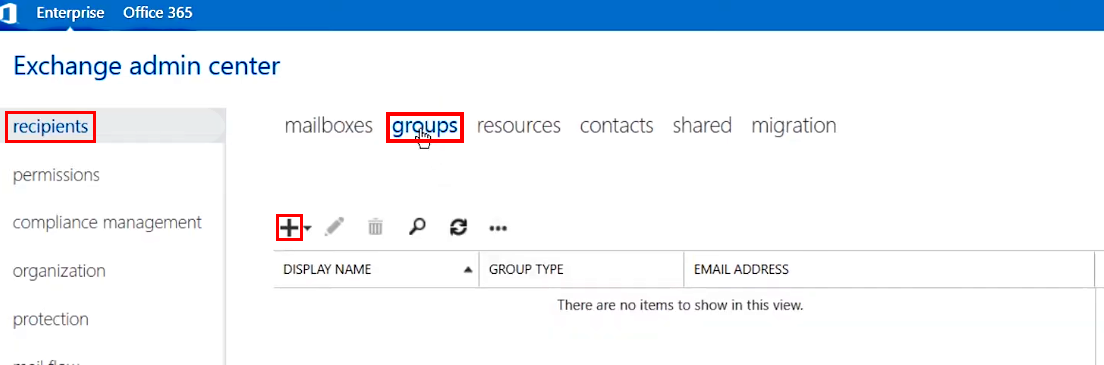
2.A.3. Create a group: click on the + (Add) icon and select Distribution group
>>> Click to see a screenshot <<<
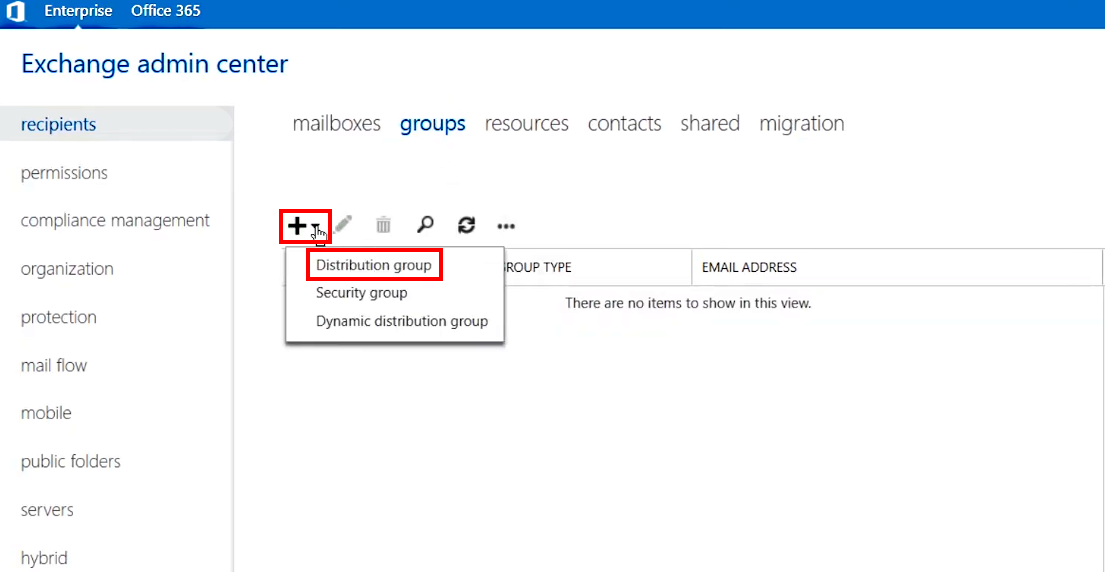
2.A.4. Enter a Display name RIapplicationGroup and an Alias RIAG to easily identify the group later
>>> Click to see a screenshot <<<
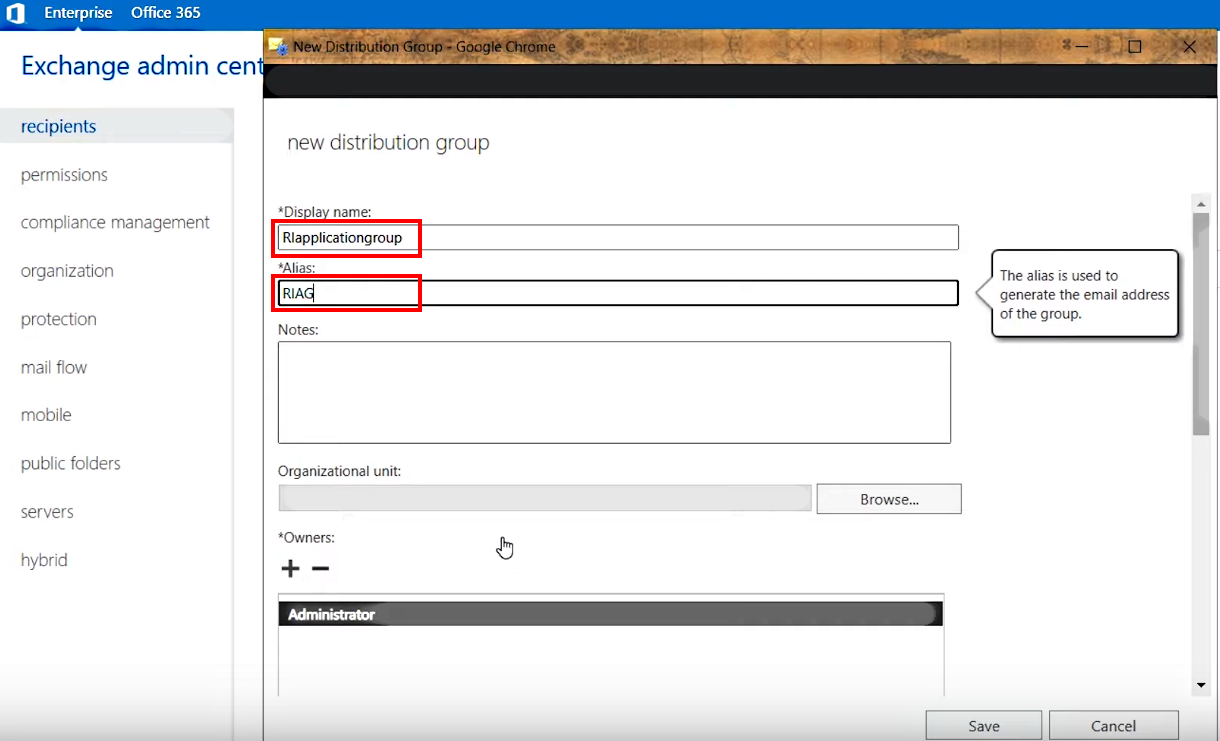
2.A.5. Next, assign the Impersonation account as a group owner:
- Click the + (Add) icon under Owners:
>>> Click to see a screenshot <<<
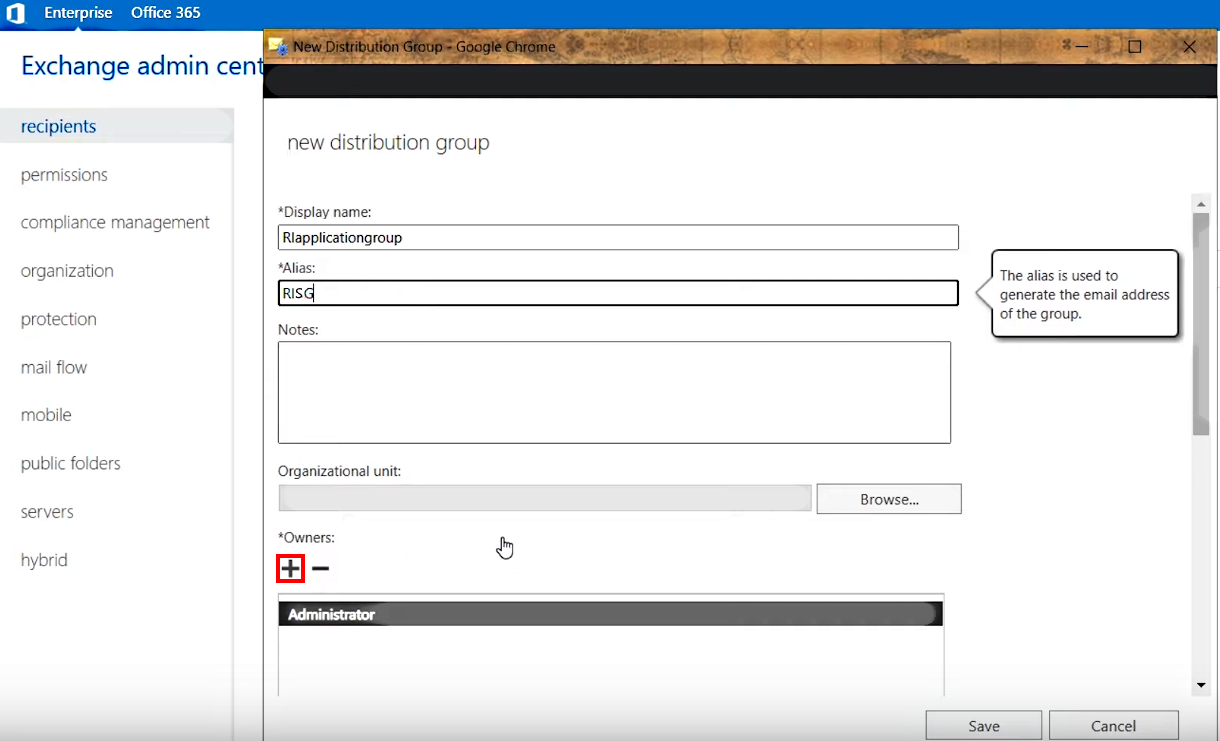
- In the dialog that appears, use the 🔍 icon to find the MasterImpersonation account you created earlier and then add - > it to group owners
2.A.6. After that, add RG Email Sidebar user accounts to the group:
-
Scroll down and make sure that the checkbox Add group owners as members is selected
-
Click the + (Add) icon under Members:
>>> Click to see a screenshot <<<
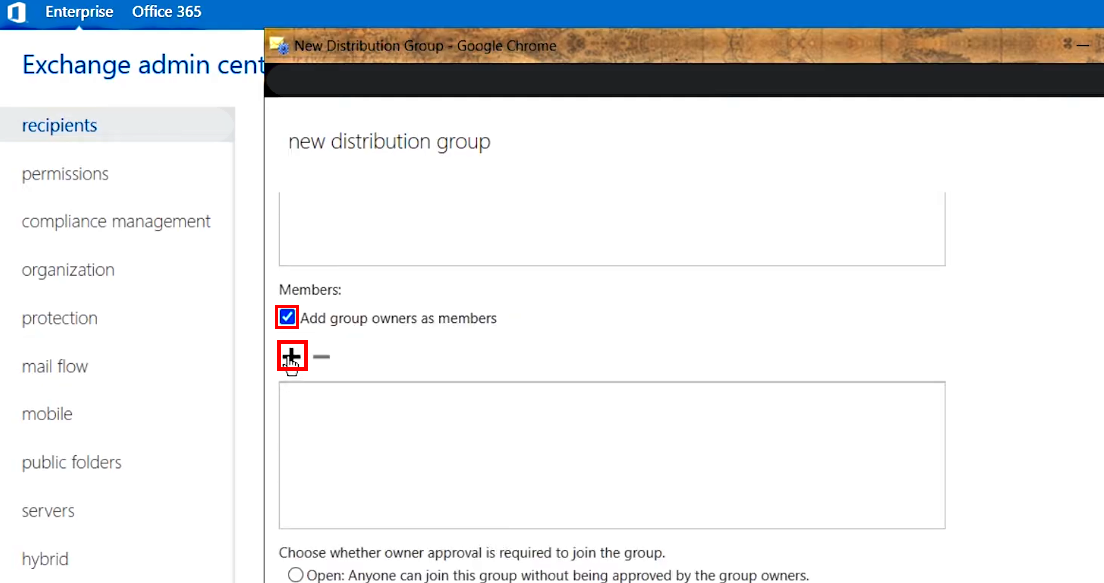
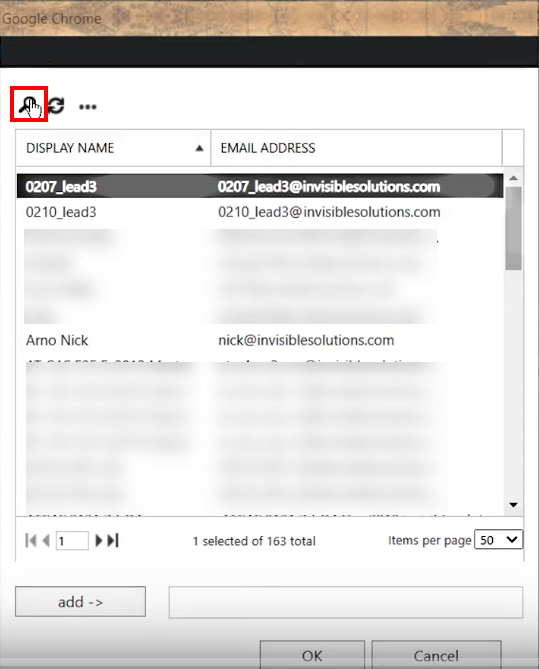
- In the dialog that appears, use the 🔍 icon to find RG Email Sidebar end users and then add - > them to the group members list
>>> Click to see a screenshot <<<
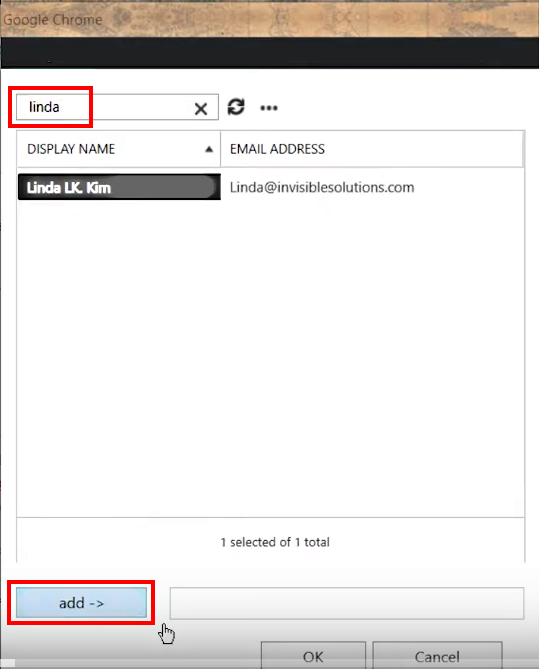
- Add all necessary users to the group in the same manner and click OK
>>> Click to see a screenshot <<<
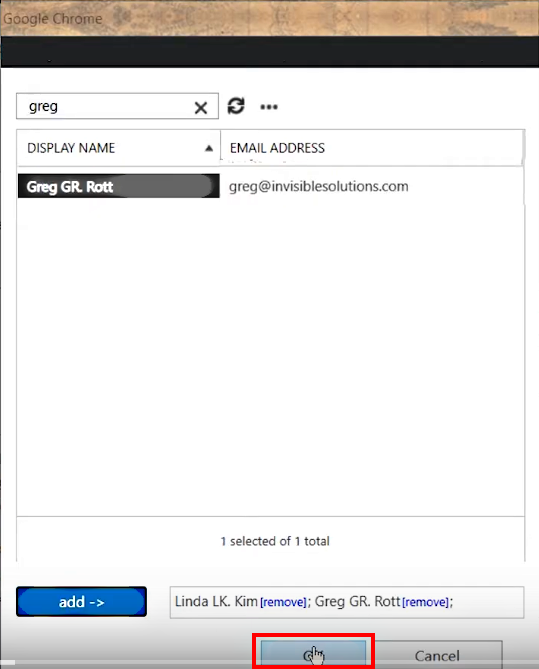
2.A.7. Set the following recommended group membership rules:
- Approval to join the group. Closed: Members can be added only by the group owners.
-
Choose whether the group is open to leave. Closed: Members can be removed only by the group owners.
-
After that, Apply the changes in the Distribution group by clicking Save at the bottom
>>> Click to see a screenshot <<<
Alternatively, if you prefer using a Security group instead
B. To create a Security group¶
2.B.1. Log in to your corporate Exchange Admin Center with Admin credentials and select the tab Exchange in the upper left corner
Exchange Admin portal link: https://admin.microsoft.com/Adminportal/Home
>>> Click to see a screenshot <<<

2.B.2. Select recipients in the navigation pane on the left and then click groups in the right-hand pane
>>> Click to see a screenshot <<<

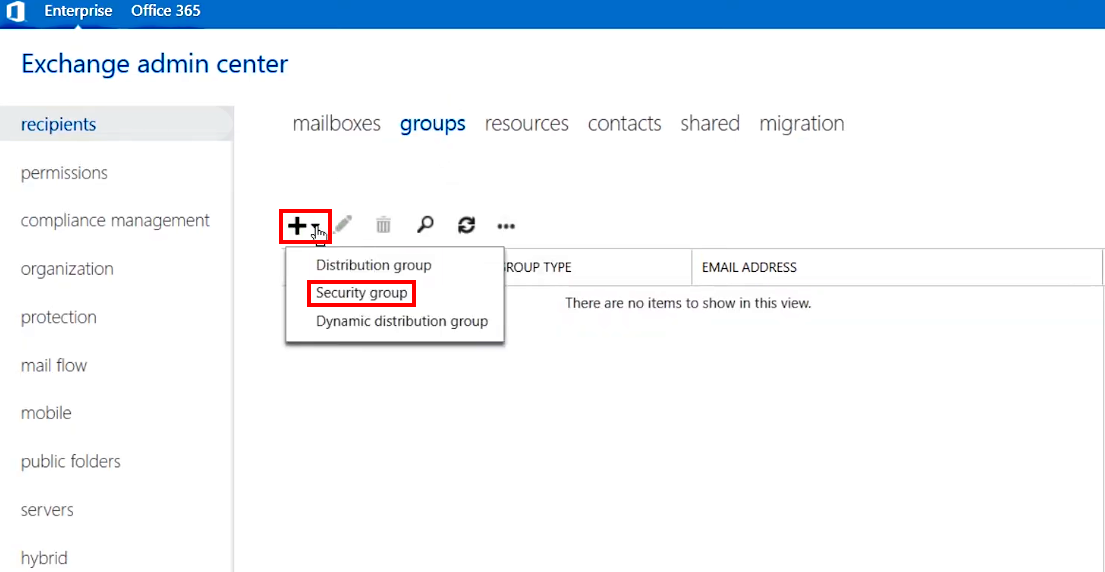
2.B.3. Create a group: click on the + (Add) icon and select Security group
>>> Click to see a screenshot <<<
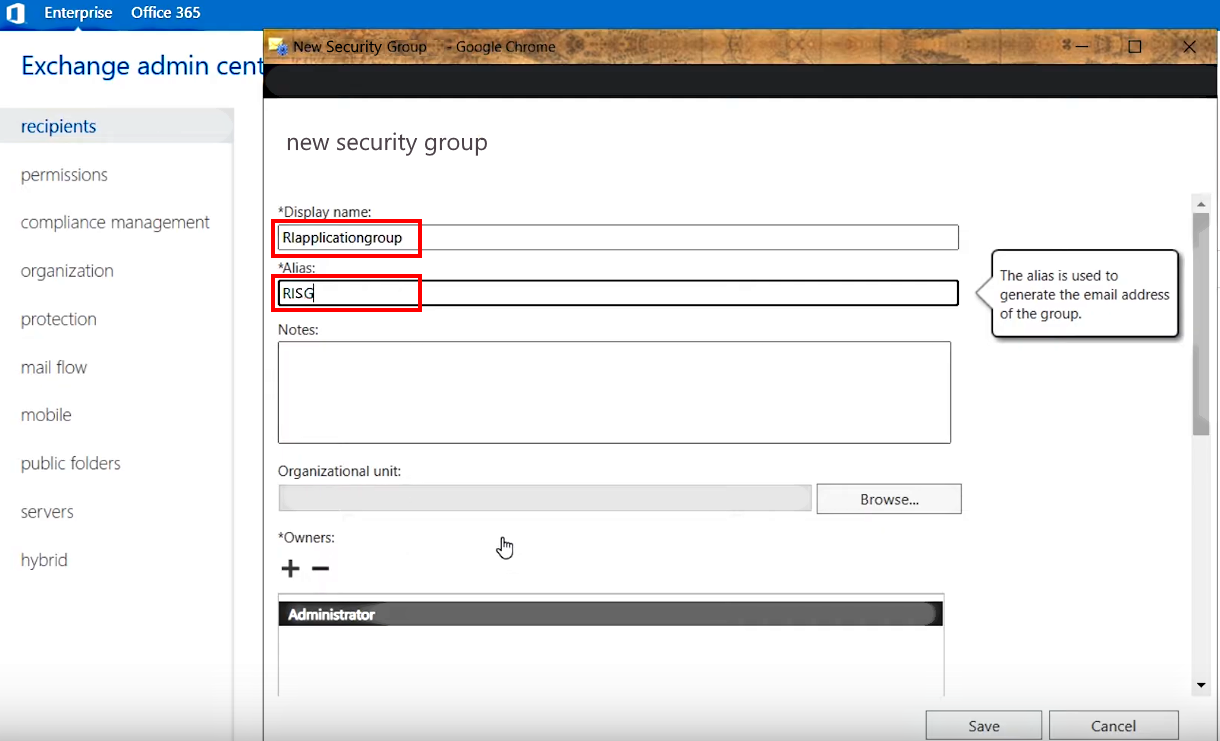
2.B.4. Enter a Display name RIapplicationGroup and an Alias RISG to easily identify the group later
>>> Click to see a screenshot <<<
2.B.5. Next, assign the Impersonation account as a group owner:
- Click the + (Add) icon under Owners:
>>> Click to see a screenshot <<<
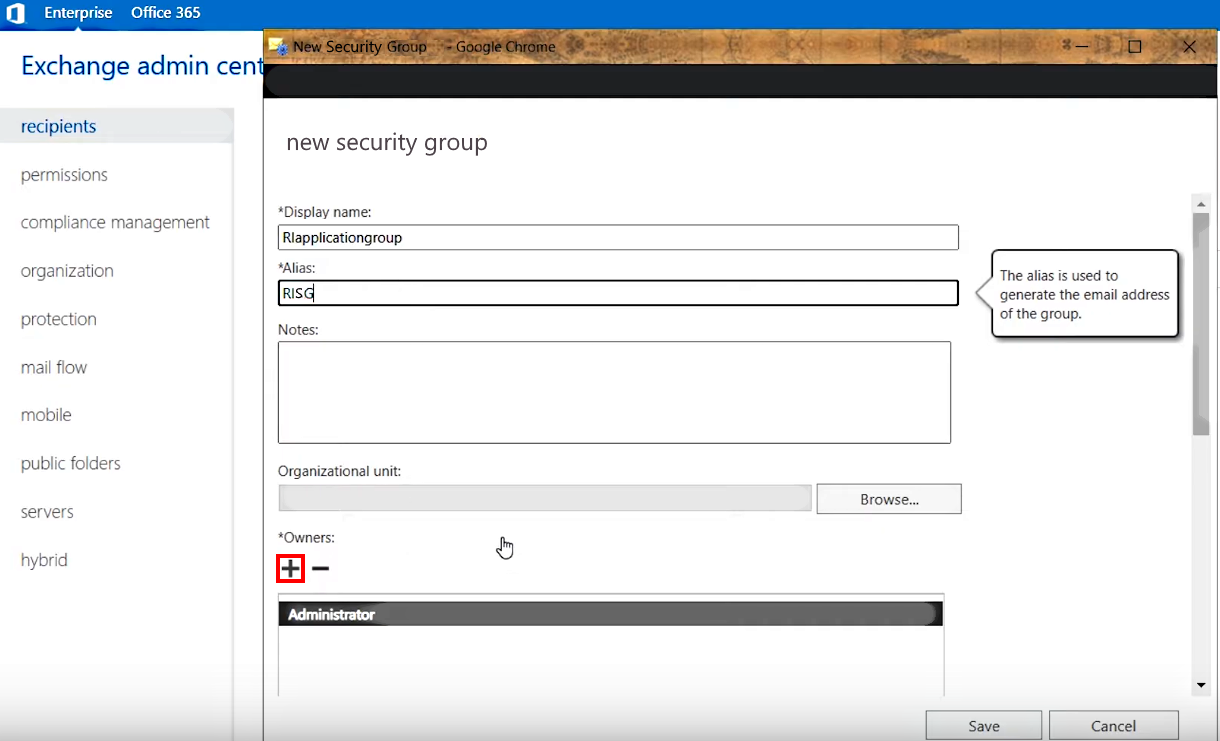
- In the dialog that appears, use the 🔍 icon to find the MasterImpersonation account you created earlier and then add - > it to group owners
2.B.6. After that, add RG Email Sidebar user accounts to the group:
- Scroll down and make sure that the checkbox Add group owners as members is selected
>>> Click to see a screenshot <<<
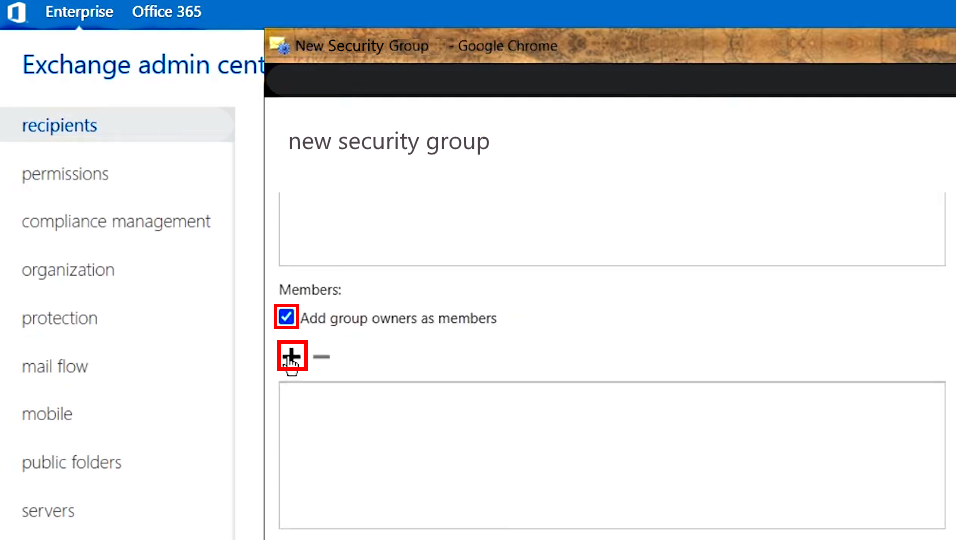
- Click the + (Add) icon under Members:
>>> Click to see a screenshot <<<

- In the dialog that appears, use the 🔍 icon to find RG Email Sidebar end users and then add - > them to the group members list
>>> Click to see a screenshot <<<


- Add all end users to the group in the same manner and click OK
>>> Click to see a screenshot <<<

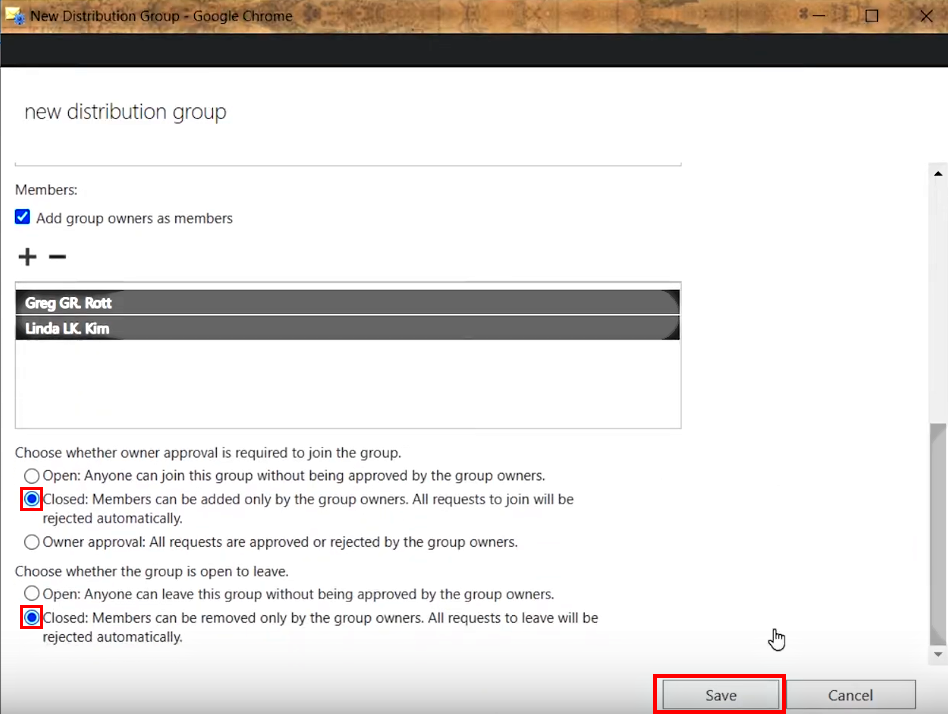
2.B.7. Enable the recommended group joining policy setting Owner approval is required by selecting a corresponding checkbox
>>> Click to see a screenshot <<<
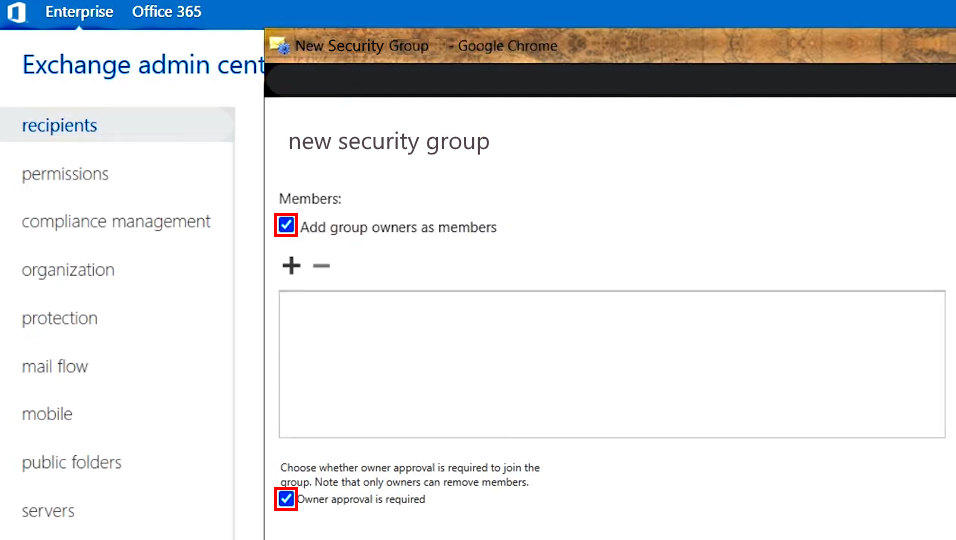
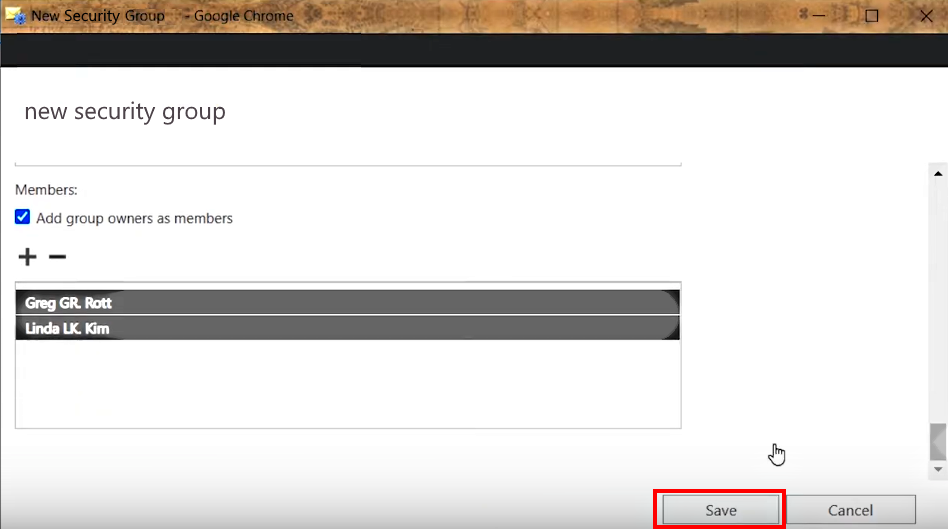
2.B.8. Apply the changes in the Security group by clicking Save at the bottom
>>> Click to see a screenshot <<<
3. Set the Users Group and Apply Impersonation¶
If you configured a Distribution group (see point 2.A. above)¶
3.A.1. Run Exchange Management Shell as Administrator
>>> Click to see a screenshot <<<
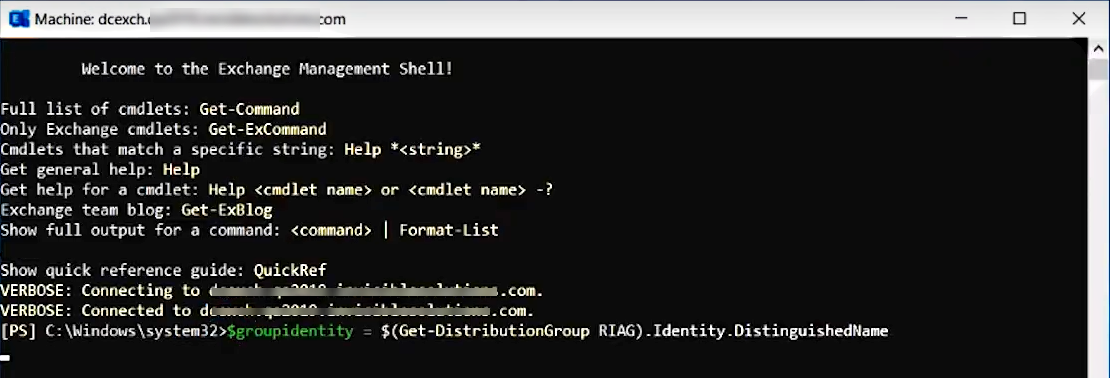
3.A.2. Enter the following lines in Exchange Management Shell console one by one:
$groupidentity = $(Get-DistributionGroup RIAG).Identity.DistinguishedName
New-ManagementScope -Name:"RIusersScope" -RecipientRestrictionFilter "MemberOfGroup -eq '$groupidentity'"
>>> Click to see a screenshot <<<
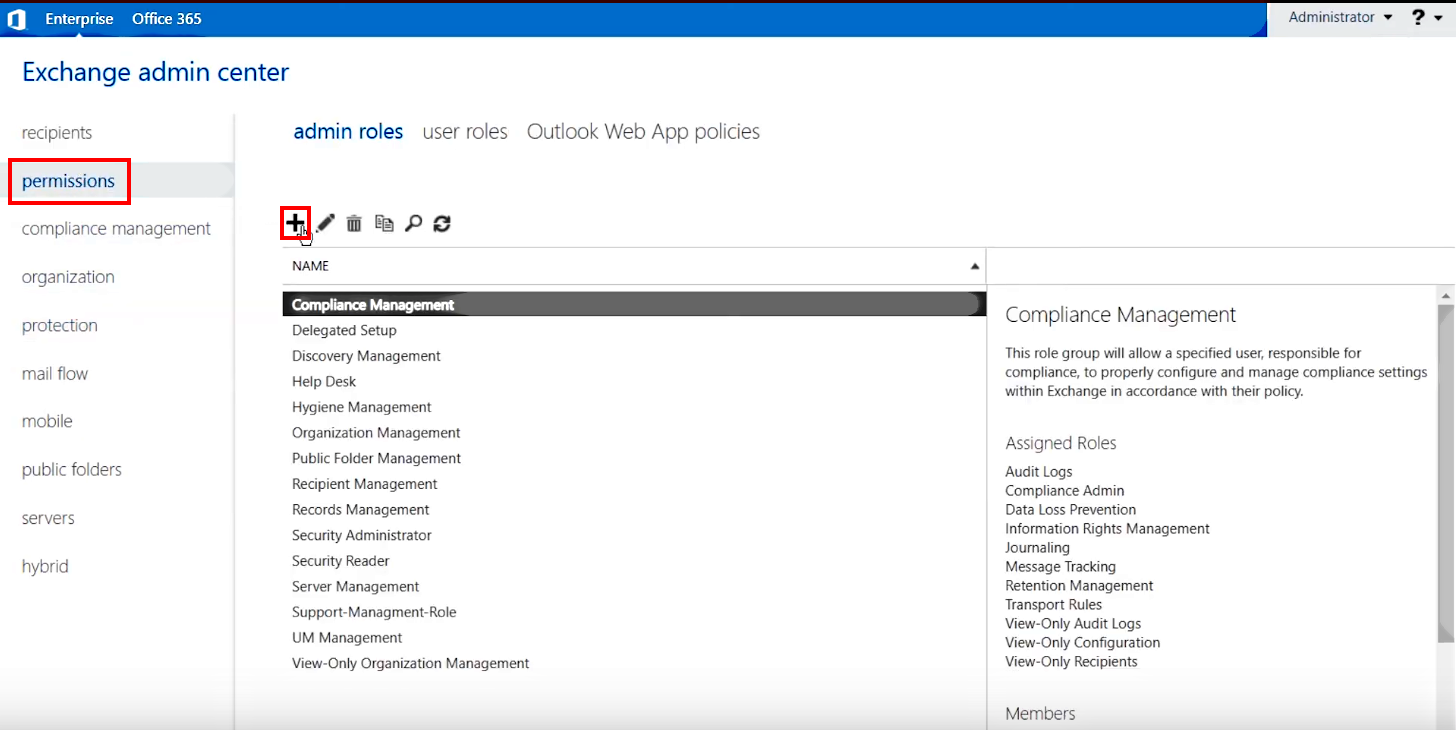
3.A.3. Next, return to Exchange Admin Center and open the permissions tab in the navigation pane on the left, then click the + (Add) icon in the header of the right pane
>>> Click to see a screenshot <<<
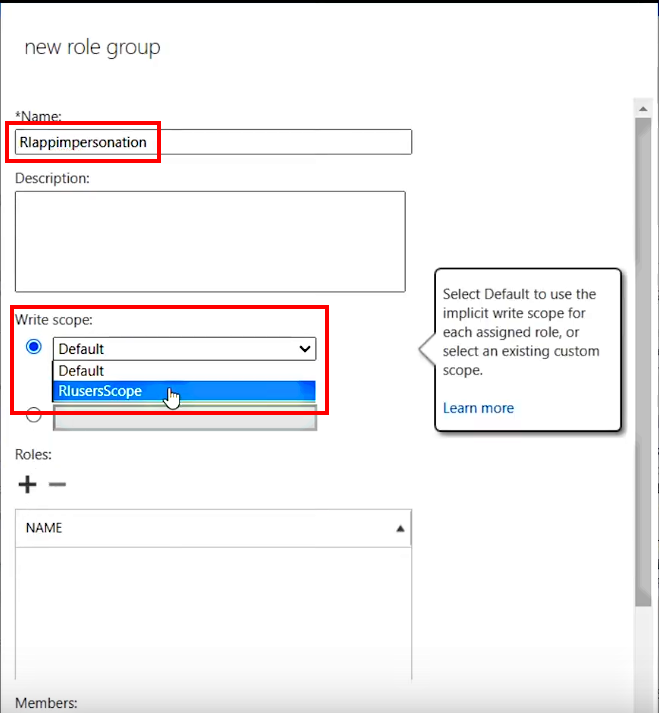
3.A.4. In the New role group dialog that appears, enter a role group’s Name, then select the RIusersScope group that you configured on Step 3.2. in the Write scope field
Tip
If you leave the Default Write scope, Impersonation will be applied for all users in the Org.
>>> Click to see a screenshot <<<
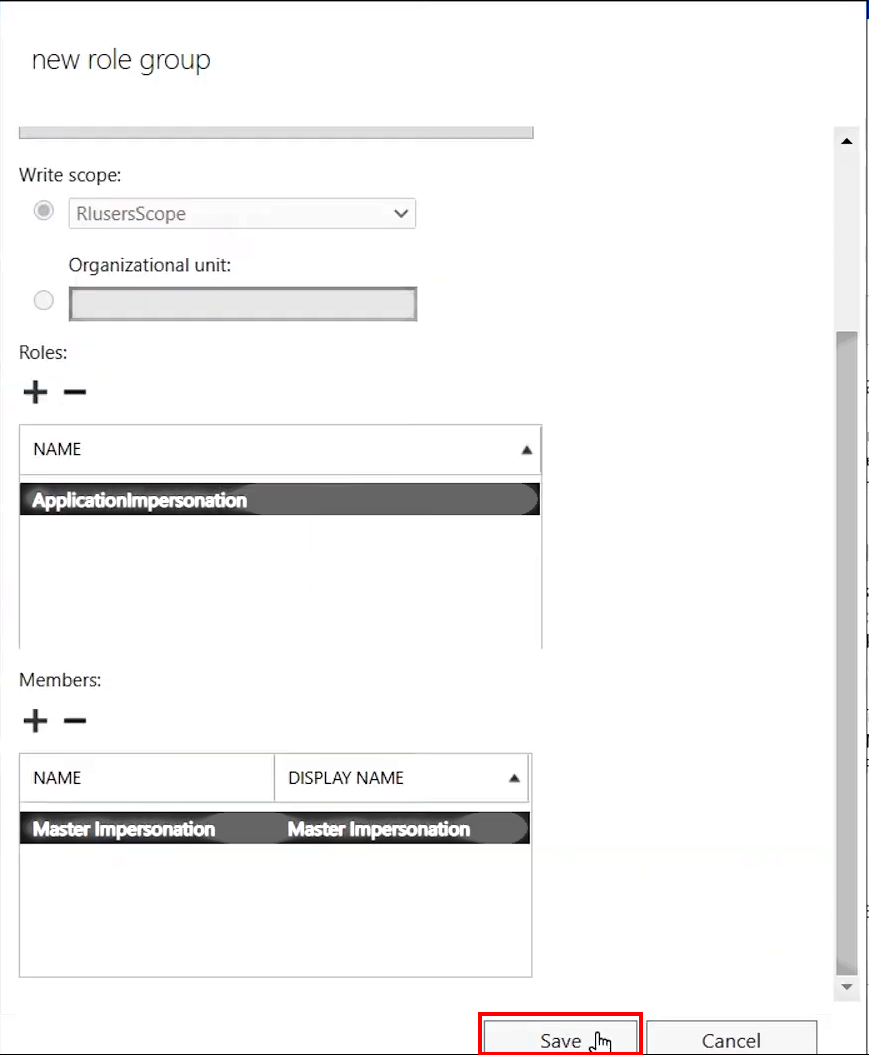
3.A.5. Next, click the + (Add) button under Roles:
>>> Click to see a screenshot <<<
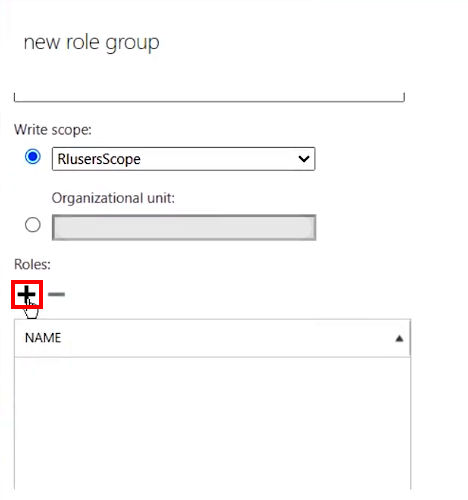
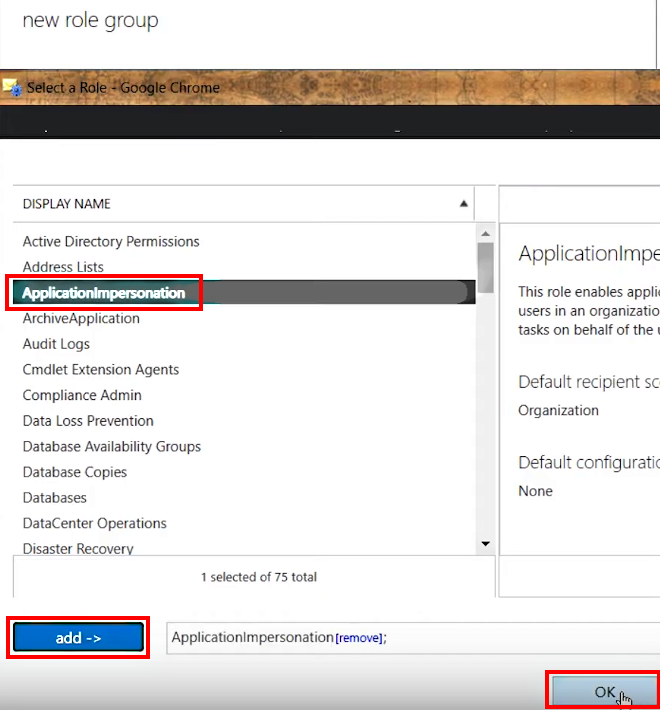
3.A.6. In the Select a Role dialog that appears, select ApplicationImpersonation in the pane on the left, then click the add - > button underneath and click OK at the bottom
>>> Click to see a screenshot <<<
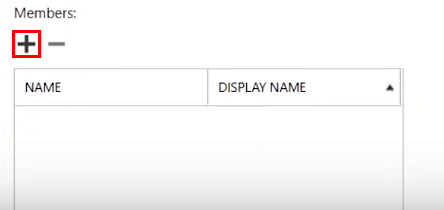
3.A.7. Now you should enable the impersonation account to perform its role. To do that:
- Next, click the + (Add) button under Members:
>>> Click to see a screenshot <<<
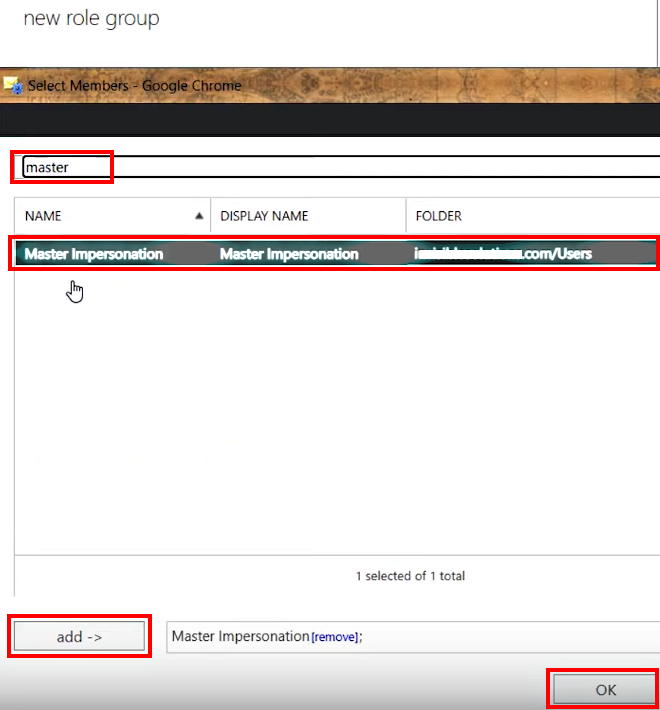
- In the Select Members dialog that appears: click the 🔍 (Search) icon and find MasterImpersonation account; select it and click the add - > button underneath, then click OK at the bottom
>>> Click to see a screenshot <<<
3.A.8. Finally, click the Save button at the bottom of the New role group dialog to apply the changes
>>> Click to see a screenshot <<<
Alternatively,
If you configured a Distribution group (see point 2.B. above)¶
3.B.1. Run Exchange Management Shell as Administrator
>>> Click to see a screenshot <<<

3.B.2. Enter the following lines in Exchange Management Shell console one by one:
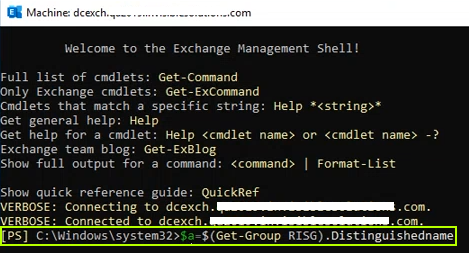
$groupidentity = $(Get-Group RISG).DistinguishedName
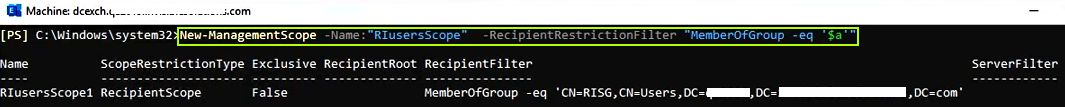
New-ManagementScope -Name:"RIusersScope" -RecipientRestrictionFilter "MemberOfGroup -eq '$groupidentity'"
>>> Click to see a screenshot <<<
3.B.3. Next, return to Exchange Admin Center and open the permissions tab in the navigation pane on the left, then click the + (Add) icon in the header of the right pane
>>> Click to see a screenshot <<<

3.B.4. In the New role group dialog that appears, enter a role group’s Name, then select the RIusersScope group that you configured on Step 3.2. in the Write scope field
Tip
If you leave the Default Write scope, Impersonation will be applied for all users in the Org.
>>> Click to see a screenshot <<<

3.B.5. Next, click the + (Add) button under Roles:
>>> Click to see a screenshot <<<

3.B.6. In the Select a Role dialog that appears, select ApplicationImpersonation in the pane on the left, then click the add - > button underneath and click OK at the bottom
>>> Click to see a screenshot <<<

3.B.7. Now you should enable the impersonation account to perform its role. To do that:
- Click the + (Add) button under Members:
>>> Click to see a screenshot <<<

- In the Select Members dialog that appears: click the 🔍 (Search) icon and find the account MasterImpersonation; click the add - > button underneath, then click OK at the bottom
>>> Click to see a screenshot <<<

3.B.8. Finally, click the Save button at the bottom of the New role group dialog to apply the changes
>>> Click to see a screenshot <<<

Stage II: Verify the Configuration¶
Next, you need to test the configured Impersonating account using the official tool Microsoft Remote Connectivity Analyzer:
1. Open Microsoft Remote Connectivity Analyzer via the link https://testconnectivity.microsoft.com
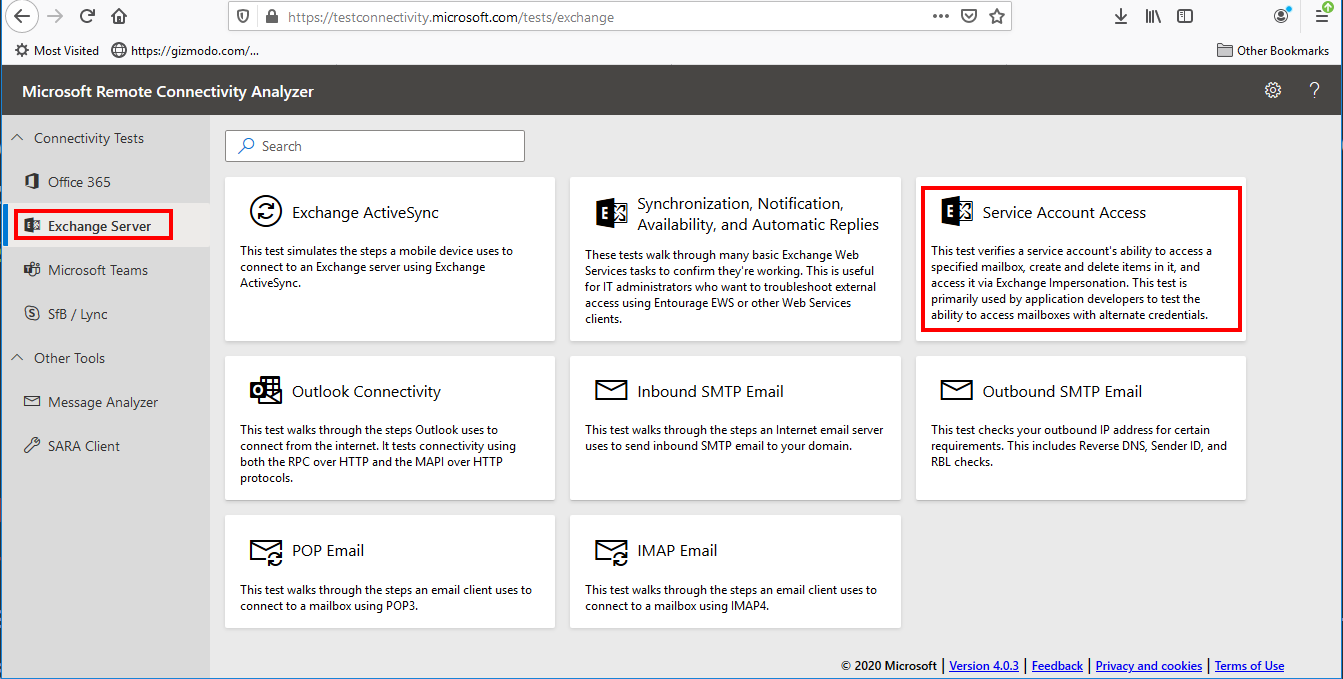
2. Open the tab Exchange Server in the navigation pane and select Service Account Access in the pane on the right
>>> Click to see a screenshot <<<
3. Fill in the details for connecting to an end user account:
4. Target Mailbox email address: enter email address of any RGES user managed by the configured Impersonation account
5. Service Account User Name (Domain\User name or UPN): enter the account’s name using the {domain}\{user name} or {user}@{domain} format
6. The Password field: enter the service account’s password
Note
Security of tested account’s credentials entered in the dialog is guaranteed by Microsoft
7. Incase your configuration has a custom Exchange Web Services URL, select Specify Exchange Web Services URL and enter your corporate EWS URL. Otherwise, select Use Autodiscover to detect server settings to let the tool auto-determine the URL
8. Next, select Test predefined folder and leave the default value Inbox in the box below
9. Select Use Exchange Impersonation and under Impersonated user enter the same email address of a RGES user managed by the configured Impersonation account
10. In the field Impersonated user identified, leave the default value SmtpAddress
11. If that is required in your configuration, select Ignore Trust for SSL
12. Read and confirm the “I understand and must …” section; enter the CAPTCHA and click Verify to prove that you are not a robot
>>> Click to see a screenshot <<<
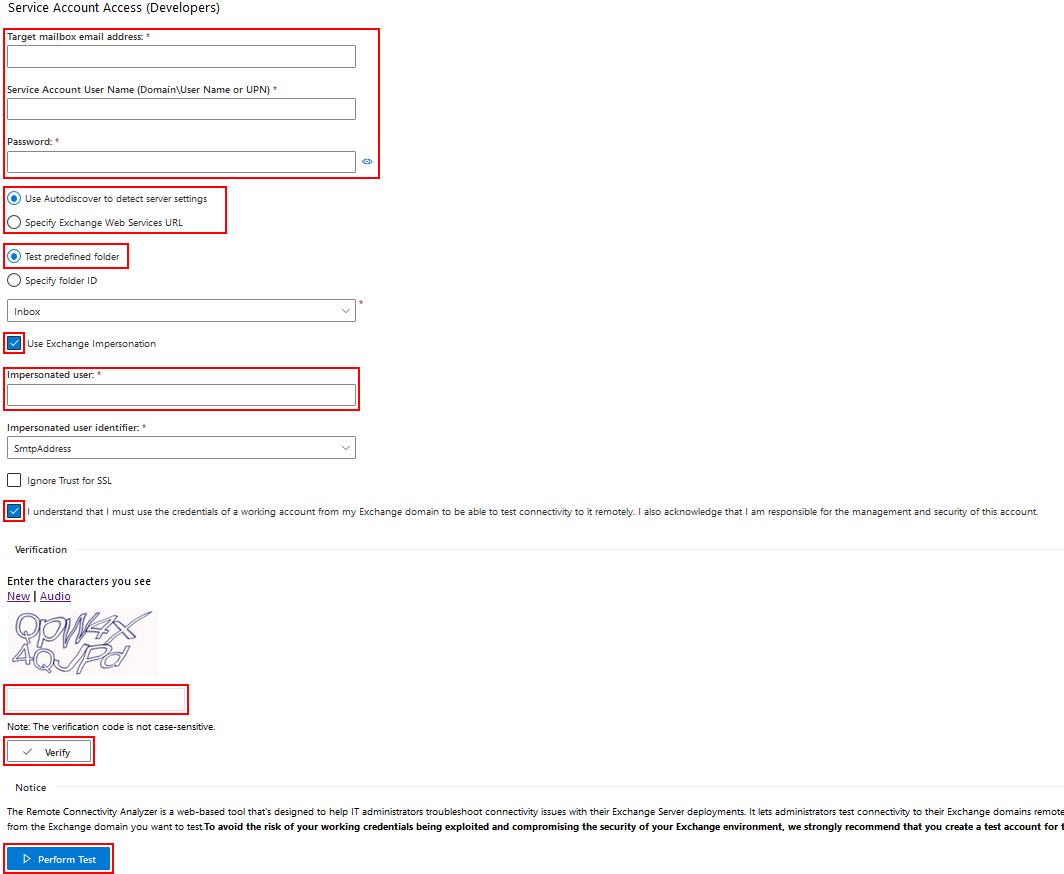
13. Click Perform test at the bottom of the dialog and check the test results to see if the configured Impersonated account works
Stage III: Configure Exchange Impersonation in RG Email Sidebar Admin panel¶
After creating a service account, proceed to the steps provided in this article to configure the Sync Engine to operate via this account.

We would love to hear from you!